
But wait a minute…
Just how can someone use this computing capacity? How many problems in the world really need the ability to calculate an enormous number of permutations with blazingly fast precision? You would be surprised. Consider the complexity of forecasting the weather, or fluid dynamics, or (wait for it…) cracking complex mathematical hashes.
If you haven’t been keeping up with the latest in Quantum Computer, here are a couple quick links for you:
https://en.wikipedia.org/wiki/Quantum_computing
https://www.nationaldefensemagazine.org/articles/2021/12/27/quantum-and-the-future-of-cryptography
https://www.ibm.com/quantum-computing/what-is-quantum-computing/
Naturally cybersecurity experts saw the promise of quantum computing and realized there were some pretty amazing tricks Qbits could be tasked to do. Encryption and decryption are perfect examples. More specifically consider something like the lowly password. How long it takes to brute force crack various password character combinations has been studied and documented numerous times over the last decade. A quick Google of the phase “password strength chart” will yield numerous graphics similar to this…
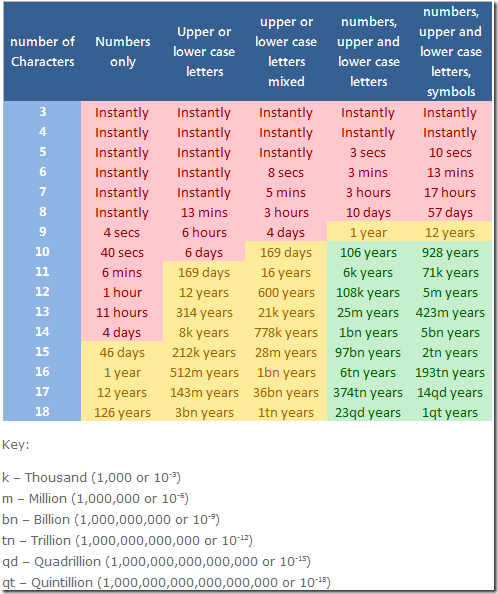
Get Cracking
Who in their right mind would spend 106 years of compute time to crack a 10 character password consisting of numbers and upper/lower case letters? You could be dead before the brute force attack finished. Obviously your no “dim bulb”. You see where this is going, right?
The only reason the crack takes 106 years is because the person who calculated that chart has to run the brute force attack serially (or at least in a very limited, parallel manner, depending on the amount of compute threads they had available to them). They have to create a password, test it against the target system, and then try another until they eventually get through.
Sure, based purely on probability, one lucky person will get it on the first try and some terribly unlucky sod will crack the password 106 years later. Most will see results somewhere under the bell curve in the range of 50 years or so. It’s just daunting.
Enter those pesky Qbits and quantum computers with their ability to calculate all possible combinations in less time that it takes to blink your eye. Suddenly what took 106 years takes mere seconds.
Or does it?
The Fallacy of Quantum Computing
Now we get to the part that no one seems to talk about or at least wants to say out loud. We have talked about cracking passwords but in reality quantum computing could be used to crack any complex mathematical probability. Certainly, for a Qbit, decrypting a SHA256 hash is only a short step up from password cracking. Change the equation, add some more Qbits and let it rip. In the end you have a nice long list of possible values with which to start cracking.
Did you catch that? I wrote, “Start cracking….”
This is where I scratch my head. Perhaps someone far smarter than I can shed some light on this but when I apply the logic of my addled brain, a little voice tells me to hold up a bit (no pun intended).
Sure, quantum computing can generate all of the possible combinations to the password for my bank account. No doubt that in very short order the quantum computer operator would have a list of passwords that would invariably contain mine. Buried in a list of password combinations, amassing somewhere in the septillions of combinations, would be the golden ticket to raid my bank account and go buy a nice dinner for yourself, on me of course.
But how does the hacker know which password works? Sure they have the list of all possible results but each will have to be tested. This is the choke point that creates the quantum decryption fallacy. While the hacker may have all the possible combinations, the only way to determine which one is correct is to test each. Unfortunately quantum computing doesn’t help with this part.
As a result, the whole Qbit cracking effort was a waste of time (sure, it was only a second or two) because there is no reasonable way to find out which password works.
My bank doesn’t have unlimited compute power and certainly isn’t going to allow for septillions of combinations to be testing without shutting my account down. As a result, the whole Qbit cracking effort was a waste of time (sure, it was only a second or two) because there is no reasonable way to find out which password works. The same goes for decryption of various hashing or encryption techniques. At some point someone or something has to validate the result. If I have a value that is encrypted, and I use a quantum computer to decrypt it, someone has to validate all possible results to determine which one is valid. That takes time. Likely way too much time to be feasible.
Defusing Hysteria
Unfortunately you have read all the way to the end and I provided no solution. My apologies. My intent was only to tamp down some of the hysteria surrounding the use of quantum computing in cybersecurity. In my opinion there was been a bit too much fear mongering about the potential for quantum computing to expose our lives (and data) to nefarious forces.
It sound’s scary on paper but in reality decryption using quantum computing simply does not exist in a vacuum. The math is only one part of the cybersecurity equation. The validation is what saves us.
So the next time someone touts the phenomenal cosmic powers of quantum computing for decryption, sit back, cross your legs comfortably, clasp your hands behind your head in a relaxed pose and ask them, “So how are you going to test that?”. You might hear an barely audible pop as a small synapsis fires somewhere deep in the recess of their brain.
